By Bex Hong Hurwitz, Tiny Gigantic
This time of pandemic and uprisings are powerful and impacting how we communicate online and offline. With more types of activities requiring us to be online from work to socializing to organizing, here are 5 ways we can move to assess and increase our and our communities’ digital safety in this time:
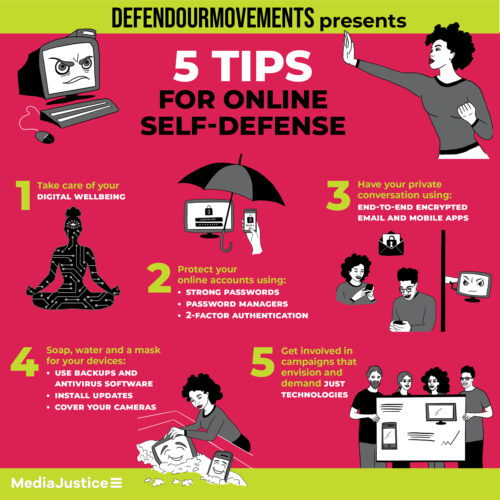
- Consider your digital wellbeing
- Take care of your online accounts using password managers and 2-Factor Authentication
- Find a way to have a private conversation using end-to-end encrypted email and mobile apps.
- Soap, water and a mask for your devices daily frequent practices to take care of your devices using backups, antivirus software, installing updates and covering our cameras
- Get involved in campaigns that envision and demand just technologies
1. Consider your digital wellbeing
Safety incidents can be an invitation to pay attention to ways that our digital activities and our wellbeing affect one another. Whether we’re experiencing harm directly (for instance through harassment online) or indirectly and empathically (for instance through watching videos of violence and documentation of harm), we can find ways of resourcing ourselves Even when we are not in the midst of responding to an incident, the time we spend online and the activities we do online have an impact on us. While everyone’s needs, boundaries, and preferences will vary, here are some questions you can start to ask to assess the impact of being online for you and for the communities you are a part of :
What are my wellbeing practices?
- How do I stay mindful of my body and mind while I am online?
- Who are my support people online and offline?
- What are my resilience practices?
Some tips
- Water, breathing, breaks. Drinking water, remembering to breathe deeply, and taking breaks to stretch and rest thumbs and fingers are a good starting place.
- Boundaries. Consider digital boundaries and how these might be part of your digital wellbeing practices. There will always be something you have not seen on the internet and many tools are designed to be addictive and demanding of your attention. What do you want to engage with online and when?
- Self-care tips from Allied Media Conference: https://amc.alliedmedia.org/how-to-virtual-amc/self-care
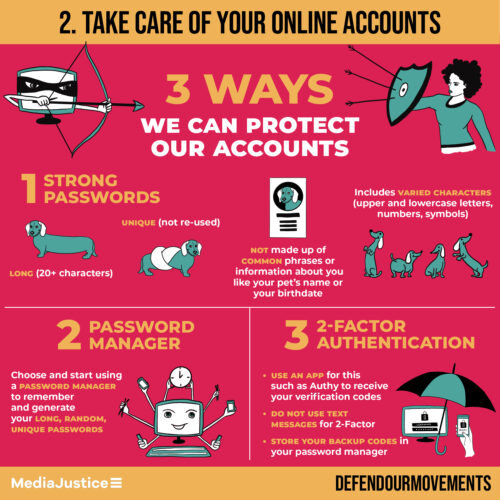
2. Take care of your online accounts
In this section:
- Strong Passwords
- Password Manager
- 2-Factor Authentication
We do a lot online, from personal and private communication, to public calls to action, to sending and receiving money. For some of us, we have been logging into accounts with usernames and passwords for many years now, and it is no longer a very strong way of protecting our accounts. We tend to reuse passwords and usernames (see this list of the most common passwords on Wikipedia), make passwords that are easy to guess or crack with a computer (test password strength here https://password.kaspersky.com/ – do not enter your actual password) and data breaches happen, when a services is hacked for password databases (go to https://haveibeenpwned.com/ to see if your accounts have been involved in data breaches).
At this point, we need more than just our favorite username/password combo to take care of our accounts. Here are 3 ways we can take care of access to our accounts.
Strong Passwords
- Use passwords that are long (20+ characters), unique (not re-used), not made up of common phrases or information about you (ex. your pet’s name, your street name, your favorite color, your favorite family member’s name, etc.), includes varied characters (upper and lowercase letters, numbers, symbols)
- Consider using passphrases; a short phrase or sentence that is significant to you and vary some characters with capital letters, numbers and symbols (for example “you park$d your C@r SIDEways”)
Password Manager
- Choose and start using a password manager to remember and generate your long, random, unique passwords.
- Keepass is a free and open source password manager you can install and keep on your own computer.
- Lastpass, Dashlane, and 1Password are products that you can access through a browser (convenient if you are using a borrowed device) or through an app that you install on your computer or mobile device. Lastpass offers a free single-user account. 1Password offers a discount to nonprofits.
- See the Defend our Movements resource on Password Managers
2-Factor Authentication (2FA)
Passwords can be stolen or taken and the best way to prevent someone from logging into your accounts if they have your password is to use 2-Factor Authentication, sometimes called 2-Step Verification.
- Use an app for this such as Authy to receive your verification codes.
- Do not use text messages (SMS) for 2-Factor whenever possible. It has become more common for people to intercept 2-Factor codes through “SIM swapping”. (Twitter CEO Jack Dorsey’s account was hacked this way.)
- Backup codes. When you set up 2-Factor Authentication, you often set up a backup method in case you cannot use your first method. For example, if you are unable to get a code from Authy on your phone for any reason, you can enter a one-time backup code or choose to receive a code in another way.
Scams attempting to get us to give away sensitive information like passwords and personal information are common. Known as phishing and spearphishing, these scams often look like an email telling us we need to urgently log into an account to fix an issue (for example, this Netflix phishing scam) or look like email sent to us from someone we know and trust asking for money or information. Our email services try to identify and warn us about emails that look like scams, but won’t catch everything.
Some protections against phishing
- 2-Factor Authentication will prevent someone from logging into your account even if they have scammed you out of your password.
- Type the website address into the browser. If you do ever receive an email asking you to log into your account, do not follow links in it. Instead, open a browser window and type the address in directly.
- Double check. If you receive any requests for sensitive information or money from someone you know, double check with them that the request is real. Call them on the phone or on a video chat and confirm with them directly.
Where to start and what to do if something goes wrong
If you do get phished or experience someone logging into your account without your consent or if your account has been part of a data breach, consider these as your first response steps:
- Log into that account from another device and change the password immediately
- If you are using the same password on any other accounts, log into those accounts and change the passwords there
- Implement 2-Factor Authentication where possible
- Check to see if there was any activity while the person was logged in – ex. posts, transfers, etc.
- Start with your most important accounts – your email accounts, financial accounts (ex. banks, credit cards, money transfer sites), and accounts you use to represent yourself publicly (ex. social media)
3. Find a way to have a private conversation
In this section:
- End-to-End Encrypted email
- End-to-End Encrypted chats and calls
By default, most of our digital communication from email and video conference calls, to text messages and voice calls on our mobile phones, is not very private. The companies and services we use to relay the communication often know and store a lot of information about our communication – from who was involved, to when and where the communication took place, to the content of the message.
At this moment, in the U.S., it is not common for us to find mobile phone carriers or internet service providers that put our privacy first, so we have to look to software and services that value privacy and our trust and use end-to-end encryption. End-to-end encryption means that a message is encoded and can only be decoded by the sender and recipient of that message. Open source is something we look for when we’re assessing if we trust the way a program is designed. Programs are made with computer code, sometimes called “source code.” An open source project is one that allows people to see all of the code that is part of a program. We look to see where a company or service and its data are located to assess how state surveillance may impact our privacy. A company that is based in the U.S. is under the jurisdiction of the U.S. and more susceptible to U.S. spying and government requests for data. A company based in and that has physical data servers outside of the U.S. is more able to resist U.S. spying.
If you are just getting started with end-to-end encryption, there are some email options and phone communication options. Whatever you choose, the people you communicate with will need to use the same system for your communication to reach each other and be protected. Some encrypted email services have ways for you to communicate end-to-end encrypted with people who don’t use the same service.
Encrypted email
- PGP encryption – https://en.wikipedia.org/wiki/Pretty_Good_Privacy – stands for “Pretty Good Privacy” which is a joke because it is actually a very strong encryption method. You can set up PGP encryption and create a “PGP encryption key” for yourself if you are using email clients like Thunderbird using the add-on Enigmail or MacMail.
- ProtonMail – https://protonmail.com – web based email that you can log into through a browser or an app where all the mail you send from one Protonmail account to another Protonmail account is PGP encrypted. You can also send encrypted email to other people who are using PGP encryption. For example, you could send a PGP encrypted email from your ProtonMail account to someone using PGP encryption on Thunderbird. Your message would be encrypted where it is stored and sent on ProtonMail as well as their email host and computer. You can communicate end-to-end encrypted with someone who cannot use PGP (ex. Gmail) by sending them an email with a link to a message and password you set and share. (More information: https://protonmail.com/support/knowledge-base/encrypt-for-outside-users/). ProtonMail is based in Switzerland.
- Tutanota – https://www.tutanota.com/ – web based email you can log into through a browser or an app. This is similar to Protonmail and all the mail you send from one Tutanota account to another Tutanota account is encrypted and you can send email to people on other services with a link to communicate end-to-end encrypted protected by a password you set and share. (More information: https://www.tutanota.com/blog/posts/email-encryption-guide-how-send-encrypted-email/. Tutanota is open source and based in Germany.
Encrypted chat and phone calls
- Signal – is an app that you can use on your phone, computer, or tablet for end-to-end encrypted chats, phone calls, video calls. Signal does not keep a record of who is communicating with whom. You will need to set it up with a phone number first and share your number for people to contact you. You can use something like a google voice number if you would like to keep your carrier phone number more private. Signal is free and open source. signal.org
- Wire – is an app that you can use on your phone, computer, or tablet for end-to-end encrypted chats, phone calls, and video calls. When you set this up, you set a screen name and share your screen name for people to contact you. It is open source and free for individual use and costs money if you want to set up a group account. wire.com
- We do not recommend relying on Whatsapp for private communication. It is using end-to-end encryption, so your message contents are private, but Whatsapp is owned by Facebook which makes its money off of watching what you do on its platforms to sell advertising to you. We should assume that Facebook is watching who we communicate with and using this to contribute to its advertising business.

4. Soap, water, and a mask for your devices
In this section:
- Backups, antivirus, check attachments and links, software updates, cover your cameras
Some basic device hygiene goes a long way.
Backups
Backing up our important information, whether it’s precious family photos or drafts of important campaign documents, reduces the impact of a computer being damaged, lost, or stolen.
- Make a list of anything that is important to you.
- Back that up somewhere safe. “Safe” means a place where you can manage access and set up some locks and keys. This might mean end-to-end encrypted cloud storage that you use a good long password and 2-Factor Authentication on, or an external hard drive that you have encrypted and stored in a locked drawer.
Antivirus
Make sure you have an antivirus program installed and set to run every day on your computer, laptop, tablets, and mobile devices. Any computer, whether it’s running Windows, MacOS or Linux, is susceptible to viruses. There are many free antivirus programs and you can choose one and run it.
Some popular ones:
- Windows 10 free built in program, Windows Defender Antivirus
- Avast, AVG, BitDefender, Kaspersky
Check attachments and links
Take care with attachments and links that you are sent electronically. Activists are periodically targeted with viruses that are downloaded through attachments and links (for example, Activists have been targeted with this virus that was sent through WhatsApp and Tibetan activists are frequently targeted with viruses through email and mobile communication). If you have any doubts, double check with senders about what they have sent before downloading or clicking. If you don’t know the sender, just don’t click!

Software Updates
Say yes to your updates. When we are shown a software update, it is most often because the software producers have become aware of a security issue and the update fixes this security issue.
Cover your cameras
Our devices have cameras and it is possible to activate these with and without our knowledge. The software that enables this is available to purchase and also used by spy agencies. A simple safety measure is to cover your camera.
- Paper and tape or the sticky part of a post-it over the camera will do
- You can find stickers made specifically as camera covers too
You can disable cameras and microphones through software settings as well. Generally, if you disable these, when you use an app or service that needs your camera or mic, it will show you a dialogue box asking your permission.
5. Get involved
And finally, getting together with others in collective action to envision and fight for an internet where we are able to speak our brave beautiful truths is one way to build more safety.
Here are a few current campaigns and organizations that you can check out and get involved in:
Stop the EARN IT Bill (campaign, Electronic Frontier Foundation) – https://act.eff.org/action/stop-the-earn-it-bill-before-it-breaks-encryption – “Senators Lindsey Graham (R-SC) and Richard Blumenthal (D-CT) are pushing forward with their so-called “EARN IT” Act, a bill that will undermine encryption and free speech online. The bill will create a new government commission, dominated by law enforcement agencies, and give it unprecedented power over websites both large and small. Attorney General Bill Barr and the DOJ have demanded for years that messaging services give the government special access to users’ private messages. If EARN IT passes, Barr will finally get his wish—law enforcement agencies will be able to scan every message sent online. The EARN IT Act (S. 3398) is anti-speech, anti-security, and unnecessary. A key Senate committee is scheduled to debate the bill next week—we need to tell Senators to reject this dangerous proposal.”
No Tech for Ice (campaign, Mijente) – https://notechforice.com/ – “Criminalization is big business. Tech companies are building the tools used to surveil, incarcerate, and deport our communities, but our communities, together with students, tech workers, and allies, are fighting back. Help us build a movement for a surveillance-free future.”
Ban Facial Recognition (campaign, Fight for the Future) – https://www.banfacialrecognition.com – “Congress just introduced a bill that would effectively ban law enforcement use of facial recognition. Send a message now to tell your members of Congress that facial recognition surveillance technology is unreliable, unjust, and a threat to basic rights and safety, and they should support the legislation to stop facial recognition!”
#ProtectBlackDissent (campaign, MediaJustice) – https://mediajustice.org/campaign/stop-spying/ – “We need your help to keep the pressure on. Sign our petition today demanding that the FBI release all documents related to the ‘Black Identity Extremist’ designation and dismantle its surveillance program targeting Black activists. The same labels of extremism are being applied to indigenous, immigrant, and AMEMSA (Arab, Middle Eastern, Muslim, South Asian) communities.”
Stop LAPD Spying (organizing in LA) – stoplapdspying.org – “Campaign to Rescind Special Order 1(1) is an alliance of different organizations (and, in our case, individuals), each with their own interests, mission and vision, that come together to collaborate and take collective action together toward a common goal(s). We reject all forms of police oppression and any policy that make us all suspects in the eyes of the State. Our vision is the dismantling of government-sanctioned spying and intelligence gathering, in all its multiple forms.”


